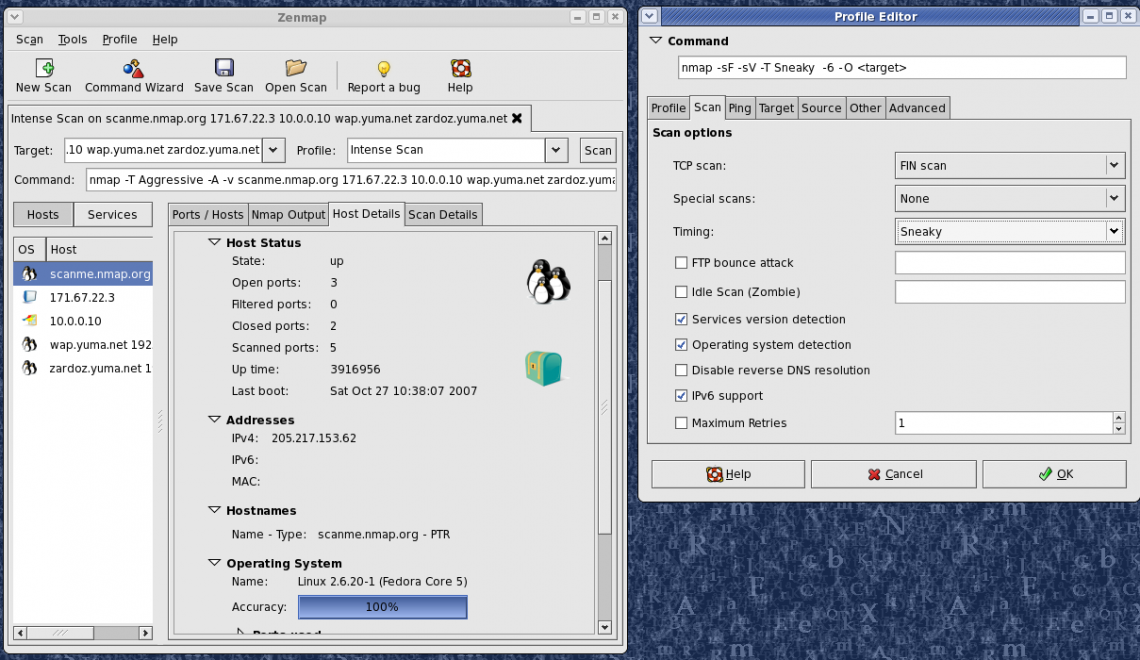
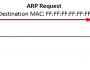
Cache poisoning is a kind of attack in which corrupted data is inserted into the cache database of DNS(Domain Name System) name server. The Domain Name System ( DNS ) is a system which associates domain names with respective IP addresses. Devices which are connected to the internet or a private network rely on the DNS for resolving URLs into their corresponding IP addresses. During a DNS cache poisoning attack, malicious party sends duplicate responses from an imposter DNS to reroute a domain name to a new IP address. The new IP address is most likely controlled by the attacker and is used to spread computer worms and other malware. Other sophisticated uses for DNS cache poisoning include denial-of-service attacks and man-in-the-middle attacks.
Cache Poisoning Attacks
Cache poisoning attacks are possible due to the existence of the exploitable vulnerabilities in DNS software.
If an attacker sent a forged or unoriginal DNS response, this duplicate response is cached by the real DNS name server. At this point, we consider the DNS cache as “poisoned.” Due to this, users that try to visit the corrupted domain will be rerouted to the new IP address chosen by the attacker. Users will continue to receive fake IP addresses from the DNS unless the poisoned cache was cleared.
DNS cache-poisoning attacks normally use elements of social engineering to make victims download the malware. The servers and websites which attackers use to replace the authentic IP addresses looks like legitimate ones but they actually contain malware in disguise. Attackers’ use of social engineering along with the fact that domain names still appear normal can make it very difficult for users to detect cache poisoning attacks. As a result, victims willingly download malicious content that they believe to be valid and from trusted sources.